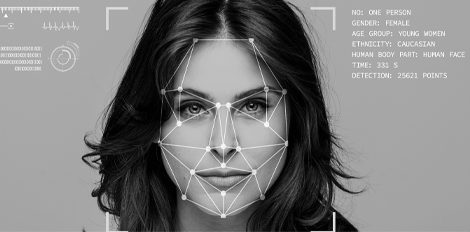
Every government-issued identity document (ID) — whether it’s a driver’s license, identity card or passport — has a specification that defines the layout of the document, the relative position of specified fields, labels and images, font types, color, size, spacing and patterns.
Every ID also contains a unique set of security features such as a ghost image, watermarks, holograms, microprint, chip and machine readable zones. These features can vary from state to state and country to country.
Jumio performs a variety of AI-driven fraud checks on these ID documents to ensure that the submitted ID conforms to these government templates and does not exhibit signs of fraudulent tampering, such as text and photo manipulation. Using informed AI, our advanced machine learning models can detect sophisticated attacks that are undetectable by the human eye.
For supplemental documentation, such as when banks require a utility bill for proof of address, Jumio scans the document and extracts its data. It can also perform fraud checks to ensure the document wasn’t manipulated or forged.

During onboarding, our face-based biometric technology compares specific facial features from the selfie — such as the distance between the eyes, nose, and ears — against those of the ID photo, ensuring they’re the same person. It also performs checks such as age estimation (does the person appear to be their stated age?) and detects whether the person is wearing a mask or is sleeping.

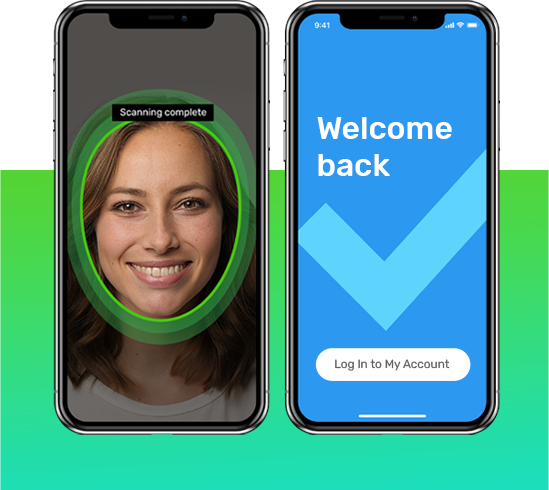
After onboarding, when the user returns to your platform, our biometric authentication solution can prompt the user to take another selfie and then compares it to the original biometric template to ensure this is the same person who onboarded.
Liveness Checks
Jumio’s advanced liveness detection technologies can detect sophisticated attacks including face swaps, face morphs and other advanced spoofing attacks. We leverage state-of-the-art AI to defeat these attacks and confirm that the person and their ID are physically present.
For example, we can determine whether the individual submits a screenshot or paper copy of a picture (i.e., a printed photo) instead of an authentic selfie — commonly referred to as a presentation attack. We can also detect video injection attacks, which involve injecting a deepfake into the digital stream by using a virtual camera or hacking the vendor’s API or SDK.

Learn about deepfakes and strategies to protect against sophisticated identity fraud.
Jumio uses advanced optical character recognition (OCR) to extract data from the user’s ID so we can compare it to the machine-readable zone (MRZ), calculate the user’s age for age verification, and more. We then check the data against a wide array of industry-leading, third-party data sources to provide an unmatched level of assurance and fraud protection to businesses worldwide.
Data checks include:
These database lookups take place in real-time from the extracted data or as an individual completes a standard onboarding form. With device checks, the information is detected from the user’s device before they’ve entered any information at all. Jumio then dynamically tailors the user’s onboarding experience based on their risk profile, introducing additional checks only as needed and minimizing friction for legitimate users.

Jumio revolutionized identity verification by pioneering selfie-based identification. Now, we’re transforming the industry once again with a new approach powered by connected data. As part of our identity analytics capabilities, Jumio Matched Transaction Lookup goes beyond traditional identity verification — which evaluates transactions in isolation — by linking identity elements across the Jumio network. This reveals patterns of both trusted and fraudulent behavior, enabling customers to detect fraud before it happens with a holistic, network-wide view of user identity.
By leveraging a dynamic blend of legitimate user and fraud data, businesses can:
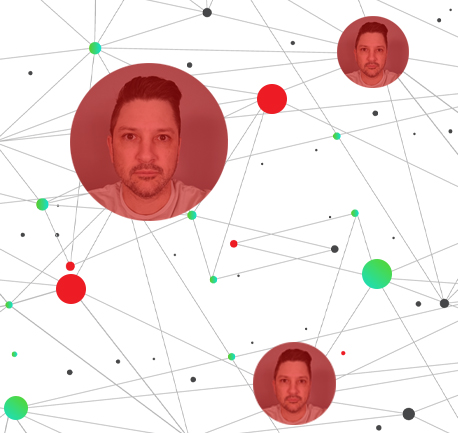
Jumio’s Matched Transaction Lookup helps businesses form a ring of protection to fight today’s fast-moving, sophisticated fraud.

The Jumio Platform provides a complete end-to-end solution for onboarding and ongoing monitoring of your users. You can orchestrate dynamic workflows that trigger identity verification, risk signals and AML screening services during the user journey based on the risk level of each user, minimizing friction for legitimate users. The real-time rules editor allows you to respond immediately to changing fraud trends. And the powerful analytics dashboard lets you easily spot trends in transactions, usage and success metrics and run detailed reports to help you maximize efficiency.
During the user journey, the AI-driven results from the various fraud checks feed into a single, unified risk score. The score calculation is configurable for your business and can be used in your workflows to trigger additional checks as needed.
One vendor. One API layer. One extremely powerful, highly secure and configurable platform. Jumio provides all of the data, business rules, orchestration, analytics and supporting tools you need to manage fraud across the user journey.
To learn more about the integration channels, see the Jumio Integration Guide.