
To beat your enemy, you have to know the enemy.
Sage counsel, indeed, written some 2,500 years ago in an influential military strategy book, “The Art of War.” Yet, what do we know of today’s digital fraudster — one who stays hidden behind the cloak of anonymity? How do organizations challenge this unknown adversary hiding in plain sight, and protect customers against identity theft and digital fraud?
What’s more, the modern fraudster is a shapeshifter depending on the fraud perpetrated — from hacker to cracker, carder, ripper, spammer, phisher, dropper and mule. And it is a face that is continually changing.
Understanding the Behavior of the Fraudster
To truly understand a fraudster’s profile, it may be useful to consider the various aspects of the fraudster’s behavior in his or her attacks.
For instance, some fraudsters will attempt to fool facial biometrics by using other people’s photos. They may even create deepfake videos from these photos to spoof the system. In March 2021, a group of scammers duped a Chinese government-run facial recognition system to falsify tax invoices. Using just a basic app and high-resolution photos bought on the black market, the fraudsters created deepfakes that were good enough to allow them to steal over US$76 million.
In other cases, fraudsters may even use their own photo but will combine this with a composite of real and fake personal data (such as names and email addresses) taken off their victims. In short, same face, different name — all to fabricate a synthetic identity that passes selfie verification.
Once they successfully gain access to the victim’s accounts, these scammers will then carry out a range of nefarious activities. They can change passwords, do an account takeover and make multiple transactions in small amounts to avoid being detected. They can also apply for credit cards to make fraudulent purchases with no intention to pay them back, and even seek loans using the victim’s account.
Synthetic identity fraud is particularly hard to detect, primarily because the victim whose information was stolen is not directly impacted. In key findings for Asia Pacific, some 61% of merchants reported higher rates of such fraud — the most among all regions globally.
Businesses should also recognize that fraudsters tend to look for the path of least resistance. SMS clickable links, for instance, are incredibly easy to exploit due to the lack of security capabilities. Victims clicking on the text message links are brought to login portals that mimic the organization’s webpage, fooling many customers. From late 2021 to early 2022, nearly 470 bank customers in Singapore lost at least S$8.5 million (US$6.13 million) to SMS phishing scams. In this case, the hackers had obtained victims’ sensitive information by posing as a trusted organization.
Various tools are used to commit fraud, including increasingly popular emulators. These are malicious software programs that run on computers and are attractive for being easy to scale up. Emulators allow cybercriminals to defraud companies by spoofing different devices and GPS locations of victims in order to pass basic checks and initiate a fraudulent transaction. These scammers can also set up emulators to make it appear as if different devices are being used to apply for new accounts. In a 2020 case, cybersecurity researchers uncovered a massive fraud operation involving a network of 20 emulators to spoof over 16,000 mobile phones. This allowed the cybercriminals to drain millions of dollars in a matter of days.
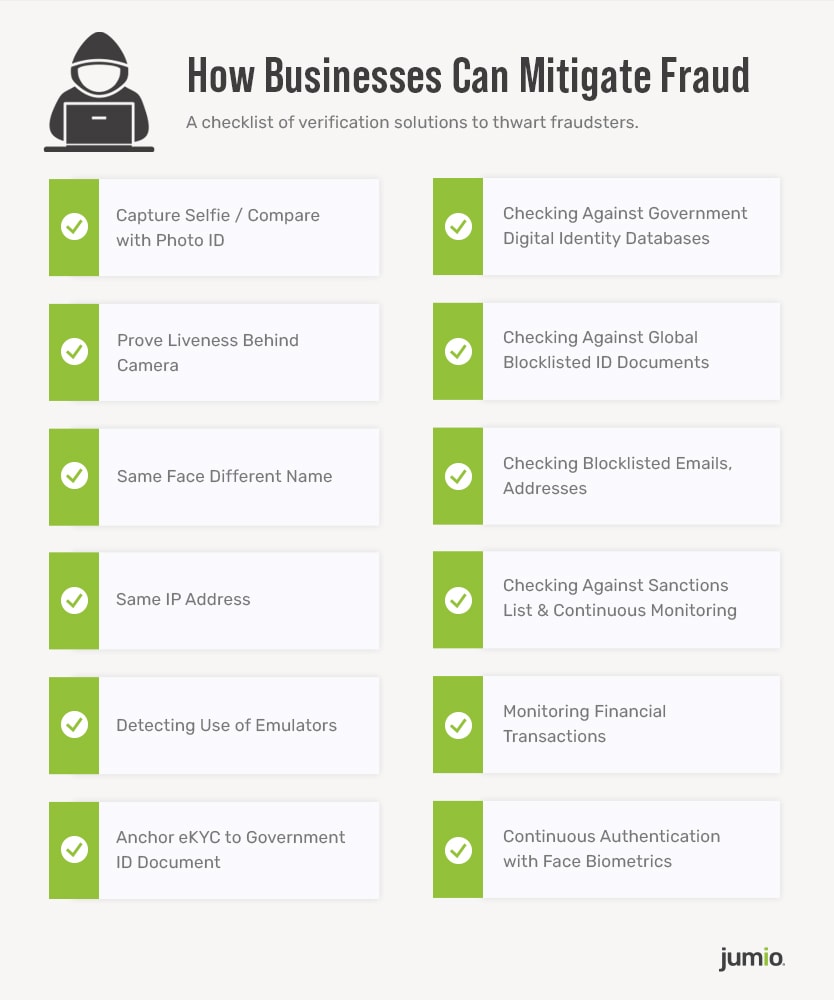
To effectively combat fraud, it is critical that businesses put in place 1) multiple verification techniques and 2) the right mix of technologies. This due diligence should be implemented throughout the customer lifecycle — from onboarding to ongoing monitoring.
During onboarding
A key finding from recent global research by Jumio found that 80% of consumers would be more likely to engage with an organization online if they had robust identity verification measures in place.
However, in designing an electronic Know Your Customer (eKYC) workflow, businesses need to do more than just conduct identity checks. These checks prove that the identity exists, but they can’t corroborate that the identity is legitimate (i.e., not synthetic), that the person producing the ID is who they claim to be, or that the user has a low-risk profile.
To handle customers’ personal information securely when signing up for an account, companies should check on other fraud signal types. These can include suspicious IP addresses and blocklisted emails. Companies can also screen submitted profiles against databases of blocklisted IDs, as fraudsters could be using the same fake ID or photo to access customer accounts on different banks and business apps.
When signing up for an account, businesses should also request the user to do selfie authentication and liveness detection checks as an additional layer of identity proofing to ensure the person is physically present and is the same person as depicted in the ID document produced. Such an approach will also act as a deterrent to the fraudsters who usually do not want to show their face.
Additionally, modern liveness detection methods are rigorously tested to ensure they can foil advanced spoofing attempts such as realistic 3D masks, among others. Hackers seeking to fool these solutions would require an unimaginable investment into expensive, bleeding-edge technologies, not to mention a lot more time and skill. Even if the investment is made, advanced liveness solutions are always evolving and will still be able to detect subtle differences.
Customer screening and risk assessment
Customer due diligence is another pillar of KYC and anti-money laundering (AML). This risk management strategy is tailored to individual customers, depending on their financial risk level and based on several factors. This includes determining whether the potential customer appears on a sanctions or watch list, is a politically exposed person (PEP), operates from high-risk locations or uses high-risk products. This will then place the potential customer in one of three levels of customer due diligence and KYC checks:
- Simplified due diligence: For customers with a low or almost non-existent risk profile for money laundering.
- Basic due diligence: Requires ID of customer and analysis of the nature of business.
- Enhanced due diligence: Aimed at high-risk customers and requires information on source of funds, the nature of business and transaction purpose.
AML screening does not end when a new account is created. Customers need to be rescreened regularly to ensure that those originally onboarded do not become financial crime risks afterward.
During transaction monitoring
To fulfill KYC, financial services companies must practice ongoing monitoring, particularly for customers with a high-risk profile. After the initial customer ID and due diligence processes are complete, businesses must create a plan that monitors financial transactions to ensure that all activities look normal.
If any customer’s transactions exhibit spikes, cross-country transactions or other unusual activity (such as multiple small amount transactions over a short period of time), they will require additional checks. This is to prove that the activity was properly authorized by the true user of the account and is not of a fraudulent or money laundering nature.
Taking an End-to-end Approach to Fraud Prevention and Financial Crime
The lines between identity proofing, online fraud detection, KYC/AML compliance and user authentication are blurring. When you sit back and look at all these identity proofing and monitoring technologies and use cases, it’s not surprising that some enterprises will deploy 10-20 different solutions to protect their ecosystems.
To stay ahead of the fast-changing cybersecurity landscape, businesses need access to flexible, multi-layered risk management platforms. These allow them to verify the identity of remote users, assess the risk of individuals and monitor their ongoing transactions — all from one platform. Because each market segment has different risk scoring requirements, implementing an integrated solution with orchestration capabilities is highly recommended. This makes it easy for businesses to configure all KYC checks needed in the customer journey based on the varying regulatory and business compliance requirements.
For a closer look at how fraudsters steal identities and what you can do to prevent them, download our free e-book, A Crisis of Identity: Understanding and Preparing for the Cyber Threat Landscape. Or contact us to learn how Jumio’s eKYC platform can help your business stay one step ahead of fraudsters.

