Financial institutions are an obvious target for cybercrime.
Unless they double down on strong internal security against a broad range of threat vectors, they will continue to be targeted and victimized by fraud rings and nation states. Unfortunately, their IT security is perceived to be deficient — especially within smaller banks and credit unions.
Making matters worse, cybercriminals are adopting new technologies, increasing their coordination and becoming more sophisticated. They’re compromising employees’ and customers’ personally identifiable information (PII) for use in illicit schemes elsewhere. Thanks to large-scale data breaches, they’re leveraging the dark web to take over legitimate accounts.
In this post, we’ll explore five emerging cybersecurity threats that financial institutions need to take seriously by building the requisite safeguards to protect their assets, customer data and reputation.
1. Identity Theft
Scary Stat: 16.7 million U.S. consumers were the victims of identity fraud last year, a record high that followed a previous record the year before, according to the 2018 Identity Fraud Study by Javelin Strategy & Research. Last year the amount stolen hit $16.8 billion and 30 percent of U.S. consumers were notified of a data breach, an increase of 12 percent from 2016.
Defined: Identity theft is the crime of using someone’s personal information, credit history or other identifying characteristics in order to make purchases or borrow money without that person’s permission.
Impact: When there’s a large-scale data breach, much of the personal information hijacked from the breach is soon be available on the dark web, where it can be bought and sold and appended to other data acquired from other breaches to perpetrate identity theft and account takeover on a grander scale. This means every time a new customer creates a new account online, the question is whether the new customer is actually who they claim to be. A natural reaction is to build in more identity checks, but this leads to increased friction and abandonment of legitimate customers.
Digital Trust Throughout the Customer Journey
How to Leverage the Jumio Platform from Onboarding to Ongoing Monitoring
2. Account Takeover
Scary Stat: Account takeovers tripled in 2017 from 2016, and losses totaled $5.1 billion, according to the 2018 Identity Fraud Study by Javelin Strategy & Research.
Defined: Using another person’s account information (e.g., a credit card number) to obtain products and services using that person’s existing accounts.
Impact: To execute an account takeover (ATO)-based email attack a cybercriminal first gains access to a trusted email account, then uses this account to launch subsequent email attacks for financial gain or to execute a data breach. ATO-based attacks are particularly dangerous and effective because they originate from email accounts of trusted senders via phishing attacks. This has two important ramifications: First, the attack is very likely to succeed because there is a pre-existing trust relationship with the customer. Second, these attacks often go undetected by traditional security controls because they originate from legitimate accounts.
3. Synthetic Fraud
Scary Stat: According to reports in The Wall Street Journal, a record $355 million in outstanding credit card debt is now owned by people who didn’t even exist as recently as 2017. By year’s end, losses from synthetic identity fraud alone could top $8 billion, and the real damage caused by fictitious people is casting doubt on the entire consumer-credit ecosystem.
Defined: Synthetic identity theft occurs when criminals create a fictitious identity using various pieces of real and fabricated information — such as a Social Security number, date of birth, address, phone number and email. The immediate victim is the bank or lender, but long-term, whoever’s Social Security number is used (this can be a child or adult), will have to deal with the impact of any accounts or debts attached to them fraudulently.
“All of it is real data and all of it will potentially check out when scanned against systems, but the real person won’t really know it’s happening because they’re only a third of the identity that’s created,” said Ryan Rasske, CERP, CAFP, American Bankers Association’s SVP responsible for serving bankers in risk and compliance area.
Impact: By all appearances, these fictitious people can seem like ideal customers, with multiple “proof of life” indicators, including their own social media profiles. And when they take out credit, they tend to pay bills promptly and nurture accounts for months or even years — only to max them out and never repay them. It’s important to note that monetary losses are just part of the whole story — financial institutions also need to dedicate time, energy and resources to chase down these non-existent identities.
What’s particularly worrisome about this new method of compromising the systems used to validate identities at account opening is that it’s working. In the short-term, lack of technology to connect an ever-growing set of data points can make a fraudster’s job easier, but in the future AI-powered tech will likely be part of the solution.
4. Ransomware
Scary Stat: In 2017, financial services were the second most targeted industry of ransomware after healthcare. Ransomware attacks actually fell nearly 30 percent over the past 12 months (source: Kaspersky’s “KSN Report: Ransomware and malicious cryptominers 2016-2018”), but financial services companies are still the second most popular industry victimized by ransomware.
Defined: A type of malicious software designed to block access to a computer system until a sum of money is paid. Ransomware is almost always triggered by an employee clicking on a link in a phishing email that they shouldn’t and clicking the link ignites the malware.
Impact: It is non-negotiable for financial services companies to maintain the privacy of their customers and the security of their confidential data. If a bank or credit union is hit with a ransomware attack, significant backlash is undoubtedly going to ensue — especially if customer data is held ransom for a significant amount of time.
5. Social Engineering
Scary Stat: Today, only about 3 percent of malware tries to exploit an exclusively technical flaw. The other 97 percent target instead users through social engineering, according to KnowBe4. Nearly 60 percent of security leaders say their organizations may have fallen victim to social engineering within just the past 12 months.
Defined: Social engineering is a method of deceiving people into giving you their information, or exploiting their weakness, or laziness, to find that information. It is believed to be the most frequently used method to get into a corporation’s network these days.
Impact: Social engineering attacks are designed to trick your employees into granting access to systems or divulging information that helps attackers gain that access through low-, or often no-tech means. Social engineering attacks can come in many forms — by phone, email, snail mail, in person or through social media. So, it’s important that you train your employees to be wary.
Protecting your Financial Castle
“The digital world has transformed almost every aspect of our lives, including risk and crime, so that crime is more efficient, less risky, more profitable and has never been easier to execute,” said Steve Grobman, Chief Technology Officer for McAfee. “That’s why financial institutions of all stripes — banks, credit unions, brokerages, and payments companies — need to take a layered approach to cybersecurity and fraud prevention.”
In the chart below, we’ve outlined each of the five cyber threats and the defense strategies that can be used to mitigate against them. For example, some of the best tactics to protect your business against identity theft (specifically how businesses can ensure that the user is who they claim to be and not a scammer who has stolen someone else’s identity) is through a combination of ID verification, biometrics and liveness detection, anomaly detection and employee training. Each of these defense strategies will be discussed in turn.
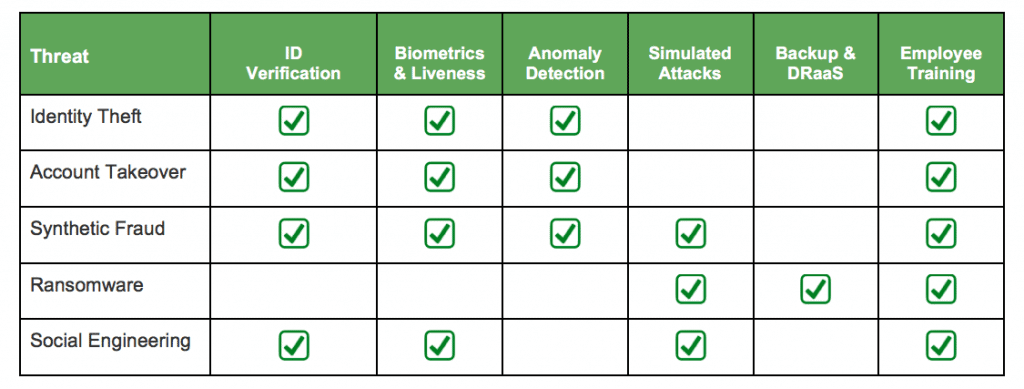
ID Verification: Require the user to provide a government-issued ID document (e.g., a driver’s license or passport) as part of the onboarding (account setup) process.
Biometrics & Liveness: Behavioral biometric technology is rising in popularity thanks to new European banking rules, the rise of machine learning and artificial intelligence, and the never-ending drive to replace passwords.
Since ID documents can be stolen and forged, adding some form of biometrics and liveness detection helps confirm that the user initiating transactions is the owner of the identity document. More importantly, requiring the user to take a selfie and perform a liveness check is a strong deterrent to would-be fraudsters since it means sharing their own likeness with the company they’re looking to defraud.
Anomaly Detection: There are a number of variants of these types of automated software solutions that detect anomalies in customer behavior. Behavioral biometrics is an innovative approach to user authentication that is based on the creation of a unique profile for every customer. Today, using leading-edge big data and machine learning technologies, behavioral biometrics leverages a rich mix of personal and device characteristics to distinguish between legitimate customers and fraudsters. Typically this includes automatic recognition of patterns (e.g., how keystrokes are made on a phone or tablet) and how a mouse is used. These human traits are reinforced with device-based indicators such as IP addresses and geo-location. Banks can analyze anomalous behavior (based on a biometric-based footprint) to spot suspicious activity and trigger real-time authentication to help stop fraudulent money movements.
Simulated Attacks: With over 90 percent of network breaches starting with a phishing email, businesses need to deploy a managed service for simulated email campaigns that help condition employees to be resilient to phishing attacks. A number of services exist to provide such training, including periodically sending fake phishing emails to staff members and alerting them if they respond unsafely.
Backup & DRaaS: Ransomware is a prime example of “better safe than sorry.” Simplistic, non-encrypting ransomware can usually be cleansed, by restoring from a clean (uncorrupted) backup. Better still, companies can deploy a disaster recovery as a service (DRaaS) solution that provides full business continuity by restoring running systems (e.g., Exchange) in minutes.
Employee Training: Humans remain the weak link in corporate data protection. Every threat outlined in this post needs to be addressed as part of regular employee awareness training. Train your entire staff on email security, social engineering, identity verification, anomaly detection and emerging cybersecurity trends and audit their understanding with regular tests and simulated attacks.
It’s clear that there is no one-size-fits-all approach to cybersecurity readiness. It invariably requires an enterprise-wide approach tailored to the culture of your financial services organization, accounting for regulatory requirements.
Foundationally, financial services organizations need to rethink how they capture and establish digital identities of new customers and verify high-risk transactions and leverage innovative solutions to ensure that your customers are who they claim to be. I know it’s become a bit of a cliché, but cybersecurity is part of everyone’s job description.